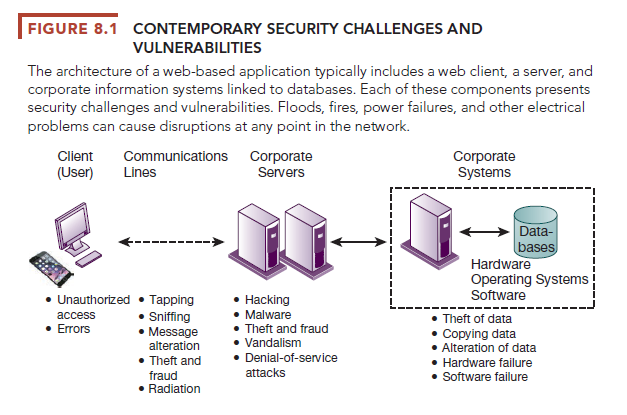
When large amounts of data are stored in electronic form, they are vulnerable to many kinds of threats. Through communications networks, information systems in different locations are interconnected. The potential for unauthorized access or damage is not limited to a single location but can occur at many access points in the network. Figure 8.1 illustrates the most common threats against contemporary information systems. They can stem from technical, organizational, and environmental factors compounded by poor management decisions. In the multitier client/server computing environment illustrated here, vulnerabilities exist at each layer and in the communications between the layers. Users at the client layer can cause harm by introducing errors or by accessing systems without authorization. It is possible to access data flowing over networks, steal valuable data during transmission, or alter data without authorization. Radiation may disrupt a network at various points as well. Intruders can launch denial-of-service attacks or malicious software to disrupt the operation of websites. Those capable of penetrating corporate systems can steal, destroy, or alter corporate data stored in databases or files.
Systems malfunction if computer hardware breaks down, is not configured properly, or is damaged by improper use or criminal acts. Errors in programming, improper installation, or unauthorized changes cause computer software to fail. Power failures, floods, fires, or other natural disasters can also disrupt computer systems.
Domestic or offshore partnering with another company contributes to system vulnerability if valuable information resides on networks and computers outside the organization’s control. Without strong safeguards, valuable data could be lost, be destroyed, or fall into the wrong hands, revealing important trade secrets or information that violates personal privacy.
Portability makes cell phones, smartphones, and tablet computers easy to lose or steal. Smartphones share the same security weaknesses as other Internet devices and are vulnerable to malicious software and penetration from outsiders. Smartphones that corporate employees use often contain sensitive data such as sales figures, customer names, phone numbers, and email addresses. Intruders may also be able to access internal corporate systems through these devices.
1. Internet Vulnerabilities
Large public networks, such as the Internet, are more vulnerable than internal networks because they are virtually open to anyone. The Internet is so huge that when abuses do occur, they can have an enormously widespread impact. When the Internet links to the corporate network, the organization’s information systems are even more vulnerable to actions from outsiders.
Vulnerability has also increased from widespread use of email, instant messaging (IM), and peer-to-peer (P2P) file-sharing programs. Email may contain attachments that serve as springboards for malicious software or unauthorized access to internal corporate systems. Employees may use email messages to transmit valuable trade secrets, financial data, or confidential customer information to unauthorized recipients. Instant messaging activity over the Internet can in some cases be used as a back door to an otherwise secure network. Sharing files over P2P networks, such as those for illegal music sharing, can also transmit malicious software or expose information on either individual or corporate computers to outsiders.
2. Wireless Security Challenges
Both Bluetooth and Wi-Fi networks are susceptible to hacking by eavesdroppers. Local area networks (LANs) using the 802.11 standard can be easily penetrated by outsiders armed with laptops, wireless cards, external antennae, and hacking software. Hackers use these tools to detect unprotected networks, monitor network traffic, and, in some cases, gain access to the Internet or to corporate networks.
Wi-Fi transmission technology was designed to make it easy for stations to find and hear one another. The service set identifiers (SSIDs) that identify the access points in a Wi-Fi network are broadcast multiple times and can be picked up fairly easily by intruders’ sniffer programs (see Figure 8.2). Wireless networks in many locations do not have basic protections against war driving, in which eavesdroppers drive by buildings or park outside and try to intercept wireless network traffic.
An intruder who has associated with an access point by using the correct SSID is capable of accessing other resources on the network. For example, the intruder could use the Windows operating system to determine which other users are connected to the network, access their computer hard drives, and open or copy their files.
Intruders also use the information they have gleaned to set up rogue access points on a different radio channel in physical locations close to users to force a user’s radio network interface controller (NIC) to associate with the rogue access point. Once this association occurs, hackers using the rogue access point can capture the names and passwords of unsuspecting users.
Source: Laudon Kenneth C., Laudon Jane Price (2020), Management Information Systems: Managing the Digital Firm, Pearson; 16th edition.

Thanks for the text it is truly an informative text, thanks for making it.
I like what you guys are up also. Such smart work and reporting! Keep up the superb works guys I have incorporated you guys to my blogroll. I think it will improve the value of my website 🙂