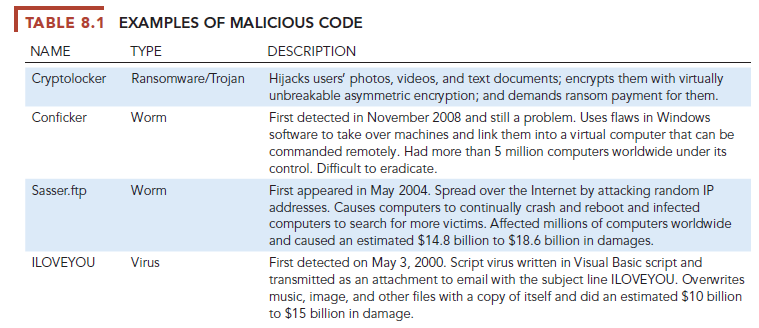
Malicious software programs are referred to as malware and include a variety of threats such as computer viruses, worms, and Trojan horses. (See Table 8.1.) A computer virus is a rogue software program that attaches itself to other software programs or data files to be executed, usually without user knowledge or permission. Most computer viruses deliver a payload. The payload may be relatively benign, such as instructions to display a message or image, or it may be highly destructive-destroying programs or data, clogging computer memory, reformatting a computer’s hard drive, or causing programs to run improperly. Viruses typically spread from computer to computer when humans take an action, such as sending an email attachment or copying an infected file.
Worms are independent computer programs that copy themselves from one computer to other computers over a network. Unlike viruses, worms can operate on their own without attaching to other computer program files and rely less on human behavior to spread rapidly from computer to computer. Worms destroy data and programs as well as disrupt or even halt the operation of computer networks.
Worms and viruses are often spread over the Internet from files of downloaded software; from files attached to email transmissions; or from compromised email messages, online ads, or instant messaging. Viruses have also invaded computerized information systems from infected external storage devices or infected machines. Especially prevalent today are drive-by downloads, consisting of malware that comes with a downloaded file that a user intentionally or unintentionally requests.
Hackers can do to a smartphone just about anything they can do to any Internet-connected device: request malicious files without user intervention, delete files, transmit files, install programs running in the background to monitor user actions, and potentially convert the smartphone to a robot in a botnet to send email and text messages to anyone. According to IT security experts, mobile devices now pose the greatest security risks, outpacing those from larger computers. Kaspersky Lab reported that it had detected 5.7 million mobile malicious installation packages in 2017 (Kaspersky Lab, 2018).
Android, which is the world’s leading mobile operating system, is the mobile platform targeted by most hackers. Mobile device viruses pose serious threats to enterprise computing because so many wireless devices are now linked to corporate information systems.
Blogs, wikis, and social networking sites such as Facebook, Twitter, and LinkedIn have emerged as new conduits for malware. Members are more likely to trust messages they receive from friends, even if this communication is not legitimate. For example, a malware strain called FacexWorm appeared inside Facebook Messenger in 2018. Clicking a link via Facebook Messenger takes the victim to a fake YouTube page, which tries to trick the user into installing a YouTube extension for the popular Chrome browser. From there the malware can steal passwords or try to steal cryptocurrency funds such as Bitcoin.
The Internet of Things (IoT) introduces additional security challenges from the Internet-linked devices themselves, their platforms and operating systems, their communications, and even the systems to which they’re connected. New security tools will be required to protect IoT devices and platforms from both information attacks and physical tampering, to encrypt their communications, and to address new challenges such as attacks that drain batteries. Many IoT devices such as sensors have simple processors and operating systems that may not support sophisticated security approaches.
Panda Security reported that in 2017 it had identified and neutralized a total of 75 million malware files, about 285,000 new samples a day (Panda Security, 2017).
Many malware infections are Trojan horses. A Trojan horse is a software program that appears to be benign but then does something other than expected. The Trojan horse is not itself a virus because it does not replicate, but it is often a way for viruses or other malicious code to be introduced into a computer system. The term Trojan horse is based on the huge wooden horse the Greeks used to trick the Trojans into opening the gates to their fortified city during the Trojan War.
An example of a modern-day Trojan horse is the ZeuS (Zbot) Trojan, which infected more than 3.6 million computers in 2009 and still poses a threat. It has been used to steal login credentials for banking by surreptitiously capturing people’s keystrokes as they use their computers. Zeus is spread mainly through drive-by downloads and phishing, and recent variants have been difficult to eradicate.
SQL injection attacks exploit vulnerabilities in poorly coded web application software to introduce malicious program code into a company’s systems and networks. These vulnerabilities occur when a web application fails to validate properly or filter data a user enters on a web page, which might occur when ordering something online. An attacker uses this input validation error to send a rogue SQL query to the underlying database to access the database, plant malicious code, or access other systems on the network. Malware known as ransomware is proliferating on both desktop and mobile devices. Ransomware tries to extort money from users by taking control of their computers, blocking access to files, or displaying annoying pop-up messages. For example, the ransomware called WannaCry that attacked computers in more than 150 countries in May 2017 encrypts an infected computer’s files, forcing users to pay hundreds of dollars to regain access. You can get ransomware from downloading an infected attachment, clicking a link inside an email, or visiting the wrong website.
Some types of spyware also act as malicious software. These small programs install themselves surreptitiously on computers to monitor user web-surfing activity and serve up advertising. Thousands of forms of spyware have been documented. Many users find such spyware annoying and an infringement on their privacy. Some forms of spyware are especially nefarious. Keyloggers record every keystroke made on a computer to steal serial numbers for software, to launch Internet attacks, to gain access to email accounts, to obtain passwords to protected computer systems, or to pick up personal information such as credit card or bank account numbers. The Zeus Trojan described earlier uses keylogging. Other spyware programs reset web browser home pages, redirect search requests, or slow performance by taking up too much computer resources.
Source: Laudon Kenneth C., Laudon Jane Price (2020), Management Information Systems: Managing the Digital Firm, Pearson; 16th edition.

Asking questions are genuinely pleasant thing if you are not understanding anything totally, however
this article gives fastidious understanding even.
Of course, what a splendid blog and enlightening posts, I surely will bookmark your site.All the Best!