Contemporary digital networks and the Internet are based on three key technologies: client/server computing, the use of packet switching, and the development of widely used communications standards (the most important of which is Transmission Control Protocol/Internet Protocol, or TCP/IP) for linking disparate networks and computers.
1. Client/Server Computing
Client/server computing is a distributed computing model in which some of the processing power is located within small, inexpensive client computers and resides literally on desktops or laptops or in handheld devices. These powerful clients are linked to one another through a network that is controlled by a network server computer. The server sets the rules of communication for the network and provides every client with an address so others can find it on the network.
Client/server computing has largely replaced centralized mainframe computing in which nearly all the processing takes place on a central large mainframe computer. Client/server computing has extended computing to departments, workgroups, factory floors, and other parts of the business that could not be served by a centralized architecture. It also makes it possible for personal computing devices such as PCs, laptops, and mobile phones to be connected to networks such as the Internet. The Internet is the largest implementation of client/server computing.
2. Packet Switching
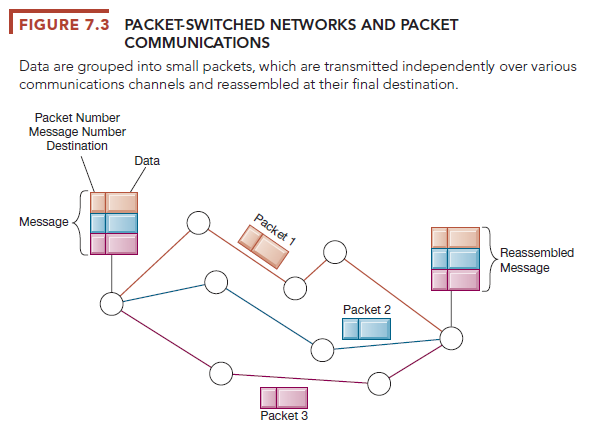
Packet switching is a method of slicing digital messages into parcels called packets, sending the packets along different communication paths as they become available, and then reassembling the packets once they arrive at their destinations (see Figure 7.3). Prior to the development of packet switching, computer networks used leased, dedicated telephone circuits to communicate with other computers in remote locations. In circuit-switched networks, such as the telephone system, a complete point-to-point circuit is assembled, and then communication can proceed. These dedicated circuit-switching techniques were expensive and wasted available communications capacity—the circuit was maintained regardless of whether any data were being sent.
Packet switching is more efficient. Messages are first broken down into small fixed bundles of data called packets. The packets include information for directing the packet to the right address and for checking transmission errors along with the data. The packets are transmitted over various communications channels by using routers, each packet traveling independently. Packets of data originating at one source will be routed through many paths and networks before being reassembled into the original message when they reach their destinations.
3. TCP/IP and Connectivity
In a typical telecommunications network, diverse hardware and software components need to work together to transmit information. Different components in a network communicate with each other by adhering to a common set of rules called protocols. A protocol is a set of rules and procedures governing transmission of information between two points in a network.
In the past, diverse proprietary and incompatible protocols often forced business firms to purchase computing and communications equipment from a single vendor. However, today, corporate networks are increasingly using a single, common, worldwide standard called Transmission Control Protocol/ Internet Protocol (TCP/IP). TCP/IP was developed during the early 1970s to support U.S. Department of Defense Advanced Research Projects Agency (DARPA) efforts to help scientists transmit data among different types of computers over long distances.
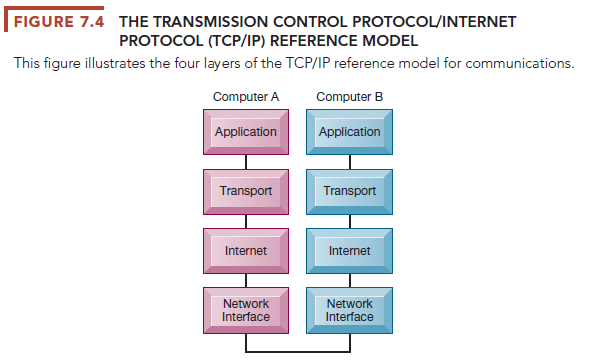
TCP/IP uses a suite of protocols, the main ones being TCP and IP. TCP refers to the Transmission Control Protocol, which handles the movement of data between computers. TCP establishes a connection between the computers, sequences the transfer of packets, and acknowledges the packets sent. IP refers to the Internet Protocol (IP), which is responsible for the delivery of packets and includes the disassembling and reassembling of packets during transmission. Figure 7.4 illustrates the four-layered Department of Defense reference model for TCP/IP, and the layers are described as follows:
- Application layer. The Application layer enables client application programs to access the other layers and defines the protocols that applications use to exchange data. One of these application protocols is the Hypertext Transfer Protocol (HTTP), which is used to transfer web page files.
- Transport layer. The Transport layer is responsible for providing the Application layer with communication and packet services. This layer includes TCP and other protocols.
- Internet layer. The Internet layer is responsible for addressing, routing, and packaging data packets called IP datagrams. The Internet Protocol is one of the protocols used in this layer.
- Network Interface layer. At the bottom of the reference model, the Network Interface layer is responsible for placing packets on and receiving them from the network medium, which could be any networking technology.
Two computers using TCP/IP can communicate even if they are based on different hardware and software platforms. Data sent from one computer to the other passes downward through all four layers, starting with the sending computer’s Application layer and passing through the Network Interface layer. After the data reach the recipient host computer, they travel up the layers and are reassembled into a format the receiving computer can use. If the receiving computer finds a damaged packet, it asks the sending computer to retransmit it. This process is reversed when the receiving computer responds.
Source: Laudon Kenneth C., Laudon Jane Price (2020), Management Information Systems: Managing the Digital Firm, Pearson; 16th edition.

Every weekend i used to pay a quick visit this
website, as i wish for enjoyment, since this this website conations
truly pleasant funny information too.
It is not my first time to pay a visit this web page, i am visiting this
website dailly and take fastidious information from here everyday.