Even with the best security tools, your information systems won’t be reliable and secure unless you know how and where to deploy them. You’ll need to know where your company is at risk and what controls you must have in place to protect your information systems. You’ll also need to develop a security policy and plans for keeping your business running if your information systems aren’t operational.
1. Information Systems Controls
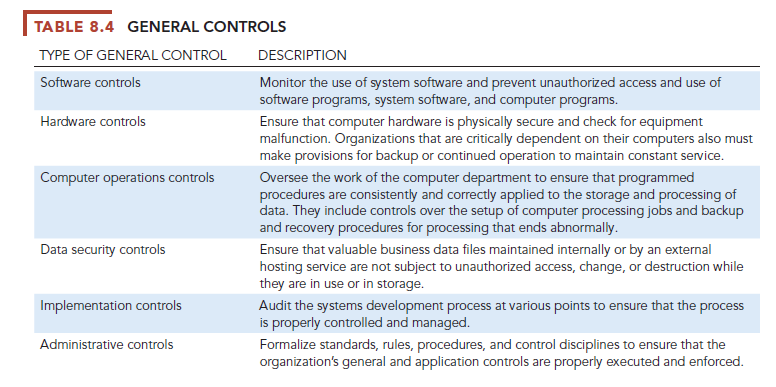
Information systems controls are both manual and automated and consist of general and application controls. General controls govern the design, security, and use of computer programs and the security of data files in general throughout the organization’s information technology infrastructure. On the whole, general controls apply to all computerized applications and consist of a combination of hardware, software, and manual procedures that create an overall control environment.
General controls include software controls, physical hardware controls, computer operations controls, data security controls, controls over the systems development process, and administrative controls. Table 8.4 describes the functions of each of these controls.
Application controls are specific controls unique to each computerized application, such as payroll or order processing. They include both automated and manual procedures that ensure that only authorized data are completely and accurately processed by that application. Application controls can be classified as (1) input controls, (2) processing controls, and (3) output controls.
Input controls check data for accuracy and completeness when they enter the system. There are specific input controls for input authorization, data conversion, data editing, and error handling. Processing controls establish that data are complete and accurate during updating. Output controls ensure that the results of computer processing are accurate, complete, and properly distributed. You can find more detail about application and general controls in our Learning Tracks.
Information systems controls should not be an afterthought. They need to be incorporated into the design of a system and should consider not only how the system will perform under all possible conditions but also the behavior of organizations and people using the system.
2. Risk Assessment
Before your company commits resources to security and information systems controls, it must know which assets require protection and the extent to which these assets are vulnerable. A risk assessment helps answer these questions and determine the most cost-effective set of controls for protecting assets.
A risk assessment determines the level of risk to the firm if a specific activity or process is not properly controlled. Not all risks can be anticipated and measured, but most businesses will be able to acquire some understanding of the risks they face. Business managers working with information systems specialists should try to determine the value of information assets, points of vulnerability, the likely frequency of a problem, and the potential for damage. For example, if an event is likely to occur no more than once a year, with a maximum of a $1000 loss to the organization, it is not wise to spend $20,000 on the design and maintenance of a control to protect against that event. However, if that same event could occur at least once a day, with a potential loss of more than $300,000 a year, $100,000 spent on a control might be entirely appropriate.
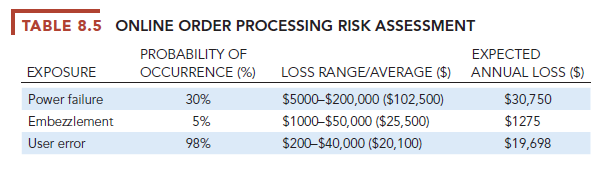
Table 8.5 illustrates sample results of a risk assessment for an online order processing system that processes 30,000 orders per day. The likelihood of each exposure occurring over a one-year period is expressed as a percentage. The next column shows the highest and lowest possible loss that could be expected each time the exposure occurred and an average loss calculated by adding the highest and lowest figures and dividing by two. The expected annual loss for each exposure can be determined by multiplying the average loss by its probability of occurrence.
This risk assessment shows that the probability of a power failure occurring in a one-year period is 30 percent. Loss of order transactions while power is down could range from $5000 to $200,000 (averaging $102,500) for each occurrence, depending on how long processing is halted. The probability of embezzlement occurring over a yearly period is about 5 percent, with potential losses ranging from $1000 to $50,000 (and averaging $25,500) for each occurrence. User errors have a 98 percent chance of occurring over a yearly period, with losses ranging from $200 to $40,000 (and averaging $20,100) for each occurrence.
After the risks have been assessed, system builders will concentrate on the control points with the greatest vulnerability and potential for loss. In this case, controls should focus on ways to minimize the risk of power failures and user errors because anticipated annual losses are highest for these areas.
3. Security Policy
After you’ve identified the main risks to your systems, your company will need to develop a security policy for protecting the company’s assets. A security policy consists of statements ranking information risks, identifying acceptable security goals, and identifying the mechanisms for achieving these goals. What are the firm’s most important information assets? Who generates and controls this information in the firm? What existing security policies are in place to protect the information? What level of risk is management willing to accept for each of these assets? Is it willing, for instance, to lose customer credit data once every 10 years? Or will it build a security system for credit card data that can withstand the once-in-a-hundred-years disaster? Management must estimate how much it will cost to achieve this level of acceptable risk.
The security policy drives other policies determining acceptable use of the firm’s information resources and which members of the company have access to its information assets. An acceptable use policy (AUP) defines acceptable uses of the firm’s information resources and computing equipment, including desktop and laptop computers, mobile devices, telephones, and the Internet. A good AUP defines unacceptable and acceptable actions for every user and specifies consequences for noncompliance.
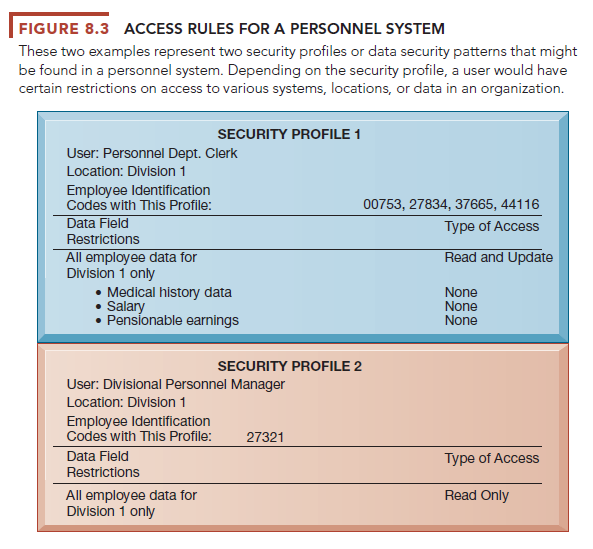
The access rules illustrated here are for two sets of users. One set of users consists of all employees who perform clerical functions, such as inputting employee data into the system. All individuals with this type of profile can update the system but can neither read nor update sensitive fields, such as salary, medical history, or earnings data. Another profile applies to a divisional manager, who cannot update the system but who can read all employee data fields for his or her division, including medical history and salary. We provide more detail about the technologies for user authentication later on in this chapter.
4. Disaster Recovery Planning and Business Continuity Planning
If you run a business, you need to plan for events, such as power outages, floods, earthquakes, or terrorist attacks, that will prevent your information systems and your business from operating. Disaster recovery planning devises plans for the restoration of disrupted computing and communications services. Disaster recovery plans focus primarily on the technical issues involved in keeping systems up and running, such as which files to back up and the maintenance of backup computer systems or disaster recovery services.
For example, MasterCard maintains a duplicate computer center in Kansas City, Missouri, to serve as an emergency backup to its primary computer center in St. Louis. Rather than build their own backup facilities, many firms contract with cloud-based disaster recovery services or firms such as SunGard Availability Services that provide sites with spare computers around the country where subscribing firms can run their critical applications in an emergency.
Business continuity planning focuses on how the company can restore business operations after a disaster strikes. The business continuity plan identifies critical business processes and determines action plans for handling mission-critical functions if systems go down. For example, Healthways, a well-being improvement company headquartered in Franklin, Tennessee, implemented a business continuity plan that identified the business processes of nearly 70 departments across the enterprise and the impact of system downtime on those processes. Healthways pinpointed its most critical processes and worked with each department to devise an action plan.
Business managers and information technology specialists need to work together on both types of plans to determine which systems and business processes are most critical to the company. They must conduct a business impact analysis to identify the firm’s most critical systems and the impact a systems outage would have on the business. Management must determine the maximum amount of time the business can survive with its systems down and which parts of the business must be restored first.
5. The Role of Auditing
How does management know that information systems security and controls are effective? To answer this question, organizations must conduct comprehensive and systematic audits. An information systems audit examines the firm’s overall security environment as well as controls governing individual information systems. The auditor should trace the flow of sample transactions through the system and perform tests, using, if appropriate, automated audit software. The information systems audit may also examine data quality.
Security audits review technologies, procedures, documentation, training, and personnel. A thorough audit will even simulate an attack or disaster to test the response of the technology, information systems staff, and business employees.
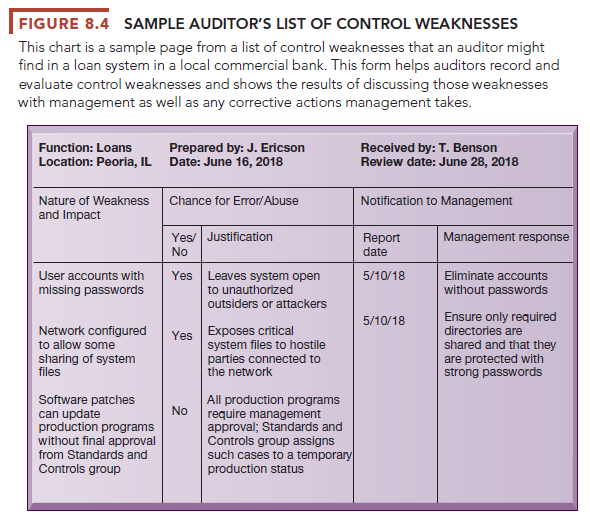
The audit lists and ranks all control weaknesses and estimates the probability of their occurrence. It then assesses the financial and organizational impact of each threat. Figure 8.4 is a sample auditor’s listing of control weaknesses for a loan system. It includes a section for notifying management of such weaknesses and for management’s response. Management is expected to devise a plan for countering significant weaknesses in controls.
Source: Laudon Kenneth C., Laudon Jane Price (2020), Management Information Systems: Managing the Digital Firm, Pearson; 16th edition.

21 Jun 2021
21 Jun 2021
21 Jun 2021
21 Jun 2021
18 Jun 2021
18 Jun 2021