September 2015, Special Agent Adrian Hawkins of the U.S. Federal Bureau of Investigation (FBI) phoned the Democratic National Committee (DNC) with troubling news about its computer network: At least one DNC computer system had been penetrated by hackers linked to the Russian government. Yared Tamene, the DNC tech-support contractor who fielded the calls, conducted a cursory search of the DNC computer system logs to look for signs of hacking. He stated that he did not look too hard, even after Special Agent Hawkins called back and left messages repeatedly over the next several weeks, because he thought the call might be a prank call from an imposter.
The DNC hack was the first sign of a Russian-led cyberwarfare campaign to disrupt the 2016 presidential election. DNC chairwoman Debbie Wasserman Schultz was forced to resign, and a torrent of confidential documents from the DNC and the Clinton campaign were released by WikiLeaks to the press during the campaign. In a stunning upset, Donald Trump won the presidential election, and his victory may have been facilitated by revelations in the leaked documents.
Several Russian hacker groups associated with Russian intelligence were identified as the source of the cyberattacks. The Russian hackers had moved freely through the DNC network for nearly 7 months before top DNC officials were alerted to the attack and hired cybersecurity firm CrowdStrike to beef up their system protection. The DNC computer system was replaced, and all laptops were turned in and their hard drives wiped clean to get rid of infected information.
In the meantime, the hackers gained access to systems of the Clinton campaign. The hackers did not have to use any sophisticated tools to gain access and were able to deploy phishing emails to trick legitimate system users into revealing passwords for accessing the system. Clinton campaign aide Charles Delavan clicked on an email sent to the personal account of campaign chairman John Podesta thinking it was legitimate and opened another door for the Russians. Whenever someone clicked on a phishing message, the Russians would enter the network, “exfiltrate” documents of interest, and stockpile them for intelligence purposes. By the summer of 2016, Democrats’ private emails and confidential documents were posted on WikiLeaks and other websites day after day and reported by the media.
The DNC thought it was well protected against cyberattacks but only had a fraction of the security budget that a corporation its size would have. It had a standard email spam-filtering service for blocking phishing attacks and malware created to resemble legitimate email, but it did not have the most advanced systems in place to track suspicious traffic.
Hacking during the 2016 presidential election went beyond the DNC and the Clinton campaign. Russian hackers tried to infiltrate at least 21 states’ election systems and to delete or alter voter data in Illinois. (Officials don’t believe the attackers changed any result.)
On July 13, 2018 a federal grand jury indicted 12 Russian intelligence officers as part of special counsel Robert Mueller’s investigation into alleged Russian meddling during the 2016 presidential campaign. The officers were charged with engaging in a sustained effort to hack networks of the Democratic Congressional Campaign Committee, the Democratic National Committee, and Hillary Clinton’s campaign. There is mounting evidence that Russian hackers are continuing to target U.S. state election systems, looking for opportunities to influence primaries, the 2018 midterm Congressional elections, and eventually the 2020 presidential campaign. Russian hackers have also been actively trying to influence elections in Europe as well.
Sources: Lucien Bruggeman and Mike Levine, “Mueller indicts 12 Russian Intel Officers for Hacking Democrats,” Good Morning America, July 13, 2018; Joseph O’Sullivan, “With Russian Hacking Fresh in Mind, Washington State Beefs Up Elections Cybersecurity,” Seattle Times, July 8, 2018; Erin Kelly, “Russia So Far Not Mounting Robust Hacking Effort Against U.S. Election, Official Says,” USA Today, July 11, 2018; Harold Stark, “How Russia ‘Hacked’ Us in 2016 [And What We did Wrong],” Forbes, January 24, 2017; Sue Marquette Poremba, “Data Security Lessons from the DNC Hack,” ITBusinessEdge, March 7, 2017; Mark Moore, “Russian Hackers Infiltrated Voter Databases in Dozens of States,” New York. Post, June 13, 2017; and Eric Lipton, David E. Sanger, and Scott Shane, “The Perfect Weapon: How Russian Cyberpower Invaded the U.S.,” New York. Times, December 13, 2016.
Efforts to disrupt the 2016 U.S presidential election and other recent elections illustrate some of the reasons why organizations need to pay special attention to information systems security. IT security breaches that enabled Russian hackers to penetrate information systems used by the Democratic Party have the potential to change the course of elections—and possibly the fate of nations. Weak IT security has been responsible for many billions of dollars of corporate and consumer financial losses as well.
The chapter-opening diagram calls attention to important points raised by this case and this chapter. The DNC and the Clinton campaign lacked IT security awareness, tools, and expertise to prevent employees from naively responding to hackers’ phishing attacks. Also at work were human ignorance, error, and carelessness, evidenced by the DNC’s unwillingness to respond quickly to the FBI’s hacker attack warning and DNC and Clinton campaign members’ inability to identify bogus phishing emails. Although the DNC and the Clinton campaign thought they had sufficient security tools to fend off unwanted intruders, they were not enough to protect them and the presidential campaign from Russian influence. Eventually the Democrats hired outside security experts to beef up system protection.
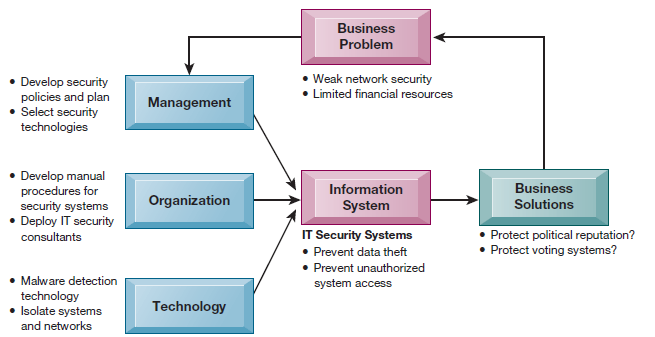
We will probably never really know exactly how much revelations from the emails exposed by the hackers affected the 2016 election outcome. But we do know that what happened was very serious and most likely a preview of future electoral trouble around the world. Equally disturbing, the security vulnerabilities that facilitated the DNC and Clinton campaign hacks are commonplace in businesses and other organizations as well.
Here are some questions to think about: What security vulnerabilities were exploited by the hackers? What management, organizational, and technological factors contributed to these security weaknesses? What was the business impact of these problems? Could the election hacking have been prevented?
Source: Laudon Kenneth C., Laudon Jane Price (2020), Management Information Systems: Managing the Digital Firm, Pearson; 16th edition.

18 Jun 2021
21 Jun 2021
21 Jun 2021
18 Jun 2021
19 Jun 2021
18 Jun 2021