Security is a prime concern of e-business managers. The principal concern is the security of information: both about customers and internal company data about finance, logistics, marketing and employees. Indeed, we saw in Chapter 4 that securing customer information is a legal requirement under data protection laws in many countries. These risks apply to all companies, large and small. Larger companies tend to be more at risk from targeted attacks which are directed at disrupting services. Information used within e-business systems must be safeguarded from a range of hazards. The range of risks faced by organizations are summarized in Box 11.3.
Given the extent of the security risks described in Figure 11.19, many organizations now implement a formal information security management system.
The information management strategy will mandate that there is an information security policy. This may be a policy developed in-house, or adoption of a security standard such as British Standard BS 7799 which has now been upgraded and ratified as international standard ISO/IEC 17799.
I have based the coverage in this edition of E-Business and E-Commerce Management on ISO 17799 since this has comprehensive coverage of different risks and approaches to management of security. It recommends the following processes:
- Plan – perform business risk analysis
- Do – internal controls to manage the applicable risks
- Check – a management review to verify effectiveness
- Act – action changes required as part of the review as necessary.
ISO 17799/BS 7799 provides an international standard which helps give a framework by which to manage the risks to the information evident from Figure 11.19. It requires the following areas of information security management to be defined:
- Section 1: Security policy. Describes the organization’s requirements and scope of security for different business areas and sites. It also should demonstrate the support of senior management in controlling and owning security.
- Section 2: Organizational security. Describes how the company manages security including different staff responsibilities for security, how security incidents are reported, actioned and reviewed as a standard business activity to improve security.
- Section 3: Asset classification and control. This is similar to completing an inventory of physical assets such as computers, printers, machinery, vehicles, etc. It requires an information audit asking questions such as ‘How much does it cost to obtain? How much would it cost to replace? What is the extent of damage done to the organization if it was disclosed to the public or a competitor?’ Through answering these questions and developing an inventory for different types of information assets, appropriate safeguards can be put in place. BS 7799 recommends that an information asset register (IAR) be created, detailing every information asset within the organization such as databases, personnel records, contracts, software licences, publicity material. For each asset, responsibility is defined. The value of each asset can then be determined to ensure appropriate security is in place.
- Section 4: Personnel security. This ensures there is clarity within job definitions and employment contracts, to reduce the risk of human error leading to information loss and to ensure that staff understand what their rights and responsibilities are concerning information security. Staff training is also important to achieve this. An example of education material which is publicly available for the Massachusetts Institute of Technology is: http://web.mit.edu/ist/topics/security/.
- Section 5: Physical and environmental security. This defines physical access to buildings. It also considers how information can be protected from threats such as fire and flood.
- Section 6: Communications and operations management. Guidelines on the day-to-day operation of information systems is the largest section of BS 7799. It covers acceptance criteria for new or updated systems, virus defence software, e-mail and web-site usage, network access and backup and restore systems.
- Section 7: Access control. This defines how to protect access to information systems through access control mechanisms (username and password procedures with different security clearance for different applications and types of information).
- Section 8: System development and maintenance. This specifies how new systems must be designed and procured with security in mind.
- Section 9: Business continuity management. Business continuity management or disaster recovery specifies how the organization will be able to continue to function in the event of a major event such as a fire or flood or other damage to information systems. Use of off-site backups and alternative systems is key to this.
- Section 10: Compliance. This specifies how an organization will comply with the relevant UK and EU law related to information security management including Health and Safety legislation – The Data Protection Act, The Computer Misuse Act, The Designs, Copyrights and Patents Act, The Human Rights Act. Implementing BS 7799 is a good way of helping ensure that a business does comply with these requirements. Regular audit and review needs to occur to ensure the organization remains compliant.
We will now cover some of the main threats to security in the e-business which need to be managed.
1. Managing computer viruses
Computer viruses are a significant threat to company and personal information since it is estimated that there are now over 100,000 of them.
1.1. Types of virus
There are many different mechanisms by which computer viruses spread from one machine to another. All use some technique for the virus to reproduce itself or ‘self-replicate’ and then pass on to another machine. We will now briefly review the main different types of computer virus companies need to protect against.
- Boot-sector virus. Boot-sector viruses were most important when floppy disks were widely used.
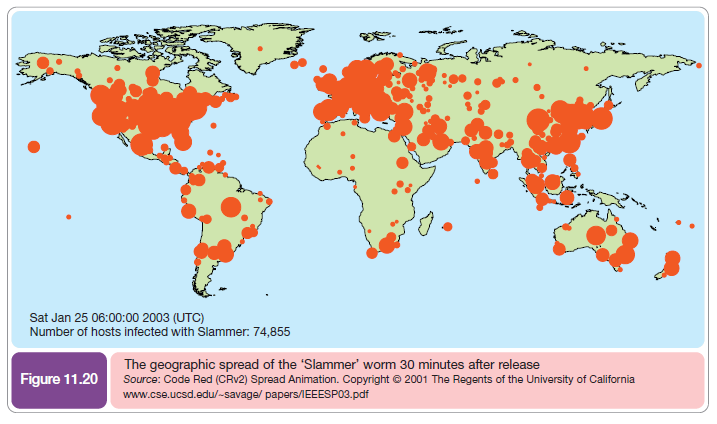
- Worms. A worm is a small computer program that replicates itself and then transfers itself from one machine to the next. Since no human interaction is required, worms can spread very rapidly. For example, the ‘Code Red’ worm replicated itself over 250,000 times in just nine hours on 19 July 2001. In 2003, the ‘Slammer’ worm exploited a security loophole in the Microsoft SQL server database product and rapidly infected 75,000 machines. Each infected machine sent out so much traffic that many other servers failed also. This was one of the fastest spreading viruses of all time, as Figure 11.20 shows. In future it seems such worms will bring the Internet to a complete standstill.
- Macro-viruses. Macro-viruses are piggybacked on documents created by office applications such as Microsoft Word and Excel. Office software such as this has a macro-facility to help users record common actions such as formatting or to develop more complex applications in Visual Basic for Applications (VBA). One of the best-known macro-viruses is ‘Melissa’. This struck in March 1999 and it marked a new trend as it combined a macro virus with one that accessed the address book of Microsoft Outlook to e-mail itself to new victims. This was one of the fastest spreading viruses in history and it is estimated that it affected over a million PCs. In 2002, the author of the ‘Melissa’ virus, David L. Smith, was sentenced to 20 months in prison in the US.

- E-mail attachment viruses. These viruses are activated when a user of an e-mail program opens an attachment. ‘Melissa’ is an example of such a virus. The ‘Love Bug’ virus contains the subject line ‘I love you’, while the message contains the text ‘kindly check the attached LOVELETTER from me’ which is an attached file called LOVE-LETTER-FOR- YOU.TXT.VBS. The virus deleted image and audio files and accessed Internet servers to send out different versions of itself. According to ClickZ (2003) it was estimated that nearly $9 billion damage was done through this virus. Much of the costs is not the loss of data, but the cost of hiring specialists to rectify the problem or staff time lost.
- Trojan viruses. A trojan is a virus that masquerades as a bona fide application. They are named after the Greek myth of the giant wooden horse used by attackers to gain access to Troy in order to attack it. Examples include utilities such as a file-sharing program, a screen saver, upgrades to some system components and even imitation anti-virus programs. The advantage for virus writers is that the programs can be much larger. One of the most famous trojans is ‘Back Orifice’, reputedly developed by a hacking group known as ‘Cult of the Dead Cow’. This could be attached to other larger files and gave complete access to a machine for a hacker.
- Hoax e-mail viruses. These are warnings about viruses which are not real viruses which ask the recipient to send the warning on to their friends. They are usually malicious, but can contain instructions on how to remove the virus by deleting files which could cause damage. They cause disruption through time lost.
1.2. Protecting computer systems against viruses
All organizations and individuals require a policy to combat the potential impact of viruses given the frequency with which new, damaging viruses are released. Even individual computer users at home should think through the steps they can take to counter viruses. There are two approaches that can be combined to counter viruses. These are using the right tools and educating staff to change practices.
Anti-virus software is well known as a tool to protect systems from viruses. Many businesses and homes now use products such as McAfee Virus Scan and Symantec Norton Anti-Virus to protect themselves against the threat of viruses. Unfortunately, a lot more action is required than initial purchase for the anti-virus software to be effective. We have seen above that new viruses are continually released. It is therefore essential that regular updates be obtained and this often doesn’t happen since a process has to be in place to trigger updates such as a monthly update.
Companies also need to decide on the frequency of scanning memory and computer files, since a full-scan on start-up can take a long time. Most anti-virus software now seeks to identify viruses when they first arrive (real-time scanning). A further issue is how good the anti-virus tool is at identifying e-mail and macro-viruses, since it is less straightforward for these types of virus to be identified.
Another approach to countering e-mail viruses is to use an external managed e-mail service which scans e-mails before they arrive in the organization and then scans e-mails for viruses when they are sent. For example, Messagelabs (www.messagelabs.com) scans 2.7billion e-mails a day for 7,500 companies worldwide. In August 2008 it reported that:
- 78% of messages were spam
- 1 in 88 contained a virus
- 1 in 522 was a phishing attempt.
Managed e-mail services are likely to be more effective than using internal anti-virus software since the service providers are experts in this field. They will also be able to identify and respond to e-mail worm attacks more rapidly.
To summarize, organizations need a policy to be developed for use of anti-virus software. This should specify:
- The preferred anti-virus software to be used on all machines.
- The frequency and mechanism for updating anti-virus software.
- The frequency with which the whole end-user PC is system-scanned for viruses.
- Organizational blocking of attachments with uncommon extensions.
- Organizational disabling of macros in office applications.
- Scanning to be performed on mail servers when e-mails are first received and before viruses are sent.
- Recommendations on use of spam-filtering software.
- Backup and recovery mechanisms.
Education of staff in identifying and then acting upon the different types of virus can also limit the impact of viruses. Apart from Internet worms which execute automatically, some steps can be taken to reduce the risks from all the types of viruses identified above. Some general instructions can then be developed as part of a policy to reduce the risk of virus infection and transmission. Many of these apply also to home machines:
- Do not switch off machines when the floppy disk is still in the drive (reduces transmission of boot-sector drives). PCs can also be configured so that they do not boot off the floppy drive.
- Do not open attachments to e-mails from people you don’t know (reduce transmission of e-mail attachment viruses). Since some viruses will be sent from trusted sources, only open attachments which look legitimate, for example Word documents with relevant names. Some viruses use file extensions that are not commonly used such as .pif, .scr or .vbs. Viewing documents rather than opening them for editing can also reduce the risk of transmission.
- Download software only from the official source, and always check for viruses before installing the software (reduces risk of trojan horse viruses).
- Disable or turn off macros in Word or Excel unless you use them regularly (reduces risk of macro-viruses).
- Back-up important files daily if this function is not performed by a system administrator.
2. Controlling information service usage
Issues in controlling information service typically involve one of two problems from the employer’s perspective. First, hardware and software resources provided for work purposes are used for personal purposes, thus reducing productivity. Secondly, monitoring the use of information introduces legal issues of surveillance. Monitoring of information service usage includes checking for:
- Use of e-mail for personal purposes.
- Inappropriate use of e-mail, possibly leading to legal action against the company.
- Use of Internet or web sites for personal use.
The problems in e-mail usage are covered in the later section on e-mail management. The extent of these issues, particularly in larger organizations is apparent from Figure 11.21.
3. Monitoring of electronic communications
Employee communications monitoring or surveillance is used by organizations to reduce productivity losses through time wasting. Time can be wasted when a member of staff spends time when they are paid to work checking personal e-mail messages or accessing the Internet for personal interests.

Simple calculations highlight the wastage when staff time is spent on non-productive work. If an employee earning £25,000 per year, spends 30 minutes each day of a 5-day week answering personal e-mails or visiting non-work-related web sites, this will cost the company over £1,500 per year. For a company with 100 employees, where the average employee works 46 weeks per year, this amounts to over £150,000 per year or the cost of several new employees! Activities such as using streaming media to view the news or download audio clips can also place strain on the company networks if they are common.
A typical example of alleged time wasting where the company dismissed the employee involved Lois Franxhi, a 28-year-old IT manager who was sacked in July 1998 for making nearly 150 searches over four days in office hours for a holiday. She claimed unfair dismissal – she was pregnant at the time of the dismissal. As with many unfair dismissals, the case was not clear-cut, with Mrs Franxhi claiming the company sacked her because of sex discrimination. The tribunal dismissed these claims, finding that the employee had lied about the use of the Internet, saying she had only used it for one lunchtime when in fact records showed she had used it over four days.
More recently DTI (2006) reported on a member of staff at a small services company who accessed adult web sites at work. He used someone else’s computer to conceal his activity. In another case, a lovesick employee at a medium-sized manufacturer spent up to six hours a day on a dating agency web site! The survey reports that
What hurts companies is the number of these incidents they suffer, more than one a day on average. While the median was only a few incidents a year, some small companies reported hundreds of e-mail abuses every day.
Communications monitoring of employees may also be warranted if it is felt they are sending or receiving e-mails or accessing web sites which contain content the organization deems unacceptable. Typical examples of such content are pornography or racist material. However, some organizations even block access to news, sports or web-based e-mail sites because of the amount of time staff spend in accessing them. To define permissible content, many organizations now have acceptable-use policies. For example, many universities, at log-in, or in computer labs and libraries have notices about ‘acceptable-use policy’. This will describe the types of material it is not acceptable to access and is also a means of explaining monitoring procedures.

Scanning and filtering are the two most common form of monitoring. Scanning software identifies the content of e-mails sent or received and web pages accessed. Tools such as WebSense or MailMarshal SMTP from Marshal or Web Marshal will look for the occurrence of particular words or images – pornography is indicated by skin colour tones for example. Rules will also be set up, for example to ban e-mail attachments over a particular size or containing swearing as indicated by Figure 11.22. Such tools can also give a picture of the most popular types of site or content. This might show, for example, how much time is being wasted accessing news and sports sites.
Such software usually also has blocking or filtering capabilities. Filtering software such as Websense (www.websense.com) can detect and block other activities such as:
- Peer-to-peer (P2P) file sharing, for example of MP3 audio files
- Instant messaging using Yahoo! Messenger or Microsoft Instant Messenger
- The use of streaming media (e.g. audio and video) and other high-bandwidth applications
- Accessing specified sites, e.g. sadly some companies block all access to social networks or news sites such as bbc.co.uk or www.msn.co.uk since analysis has shown that staff spend so much time using them. Access to personal e-mail programs such as Yahoo! Mail or Hotmail may also be blocked. This would not be popular at universities!
- Spyware which seeks to send out information collected from computers
- Adware programs which place adverts or pop-ups
- Employee hacking.
Websense and similar products can block sites in different categories, for different types of staff, according to the acceptable-use policy of the organization using a database (www. websense.com/products/about/database/categories.cfm) that contains over 1.5 million web sites in many categories of which we list just some to illustrate the degree of control available to the employer. Example of the categories include:
- Abortion or Pro-Choice or Pro-Life
- Adult Material
- Parent category that contains the categories: Adult Content, Lingerie and Swimsuit, Nudity, Sex, Sex Education
- Adult Content
- Advocacy Groups
- Business and Economy
- Financial Data and Services
- Drugs
- Education
- Entertainment
- Gambling
- Games
- Government
- Military – sites sponsored by branches or agencies of the armed services
- Political Organizations – sites sponsored by or providing information about political parties and interest groups focused on elections or legislation
- Health
- Information Technology
- Search Engines and Portals – for example, sites that support searching the web, newspapers and social networks
- Web-based E-mail – sites that host web-based e-mail
- Job Search
- Militancy and Extremist
- News and Media
- Racism and Hate
- Religion
- Shopping
- Professional and Worker Organizations
- Society and Lifestyles
- Hobbies
- Personals and Dating
- Sports
- Travel
- Vehicles
- Violence
- Weapons.
Consider how many of those listed above you may visit when studying, at business or at home. It will be apparent that if an employer wishes, they can block virtually every site. I know of some organizations in the UK that block access to all news sites and have worked in an organization that even blocked access to search engines such as Google and web mail such as Hotmail and Yahoo! Mail. When search engines are blocked, management-grade employees are likely to be restricted in their understanding of the business environment and are restricted from self-development! Employees are likely to view negatively an employer who does not trust them to use their time judiciously.
The popularity of different methods of monitoring and blocking are shown in Figure 11.23.
Employee monitoring legislation
Although employee monitoring falls within the remit of European data protection law, the Data Protection Act was not originally devised to cover employee monitoring. To help clarify the law on employee monitoring in the UK, in June 2003, the Office of the Information Commissioner published ‘Monitoring at Work’, the third part of the Employment Practices
Data Protection Code. The code provides practical guidance for employers on how they should approach monitoring of employees in the workplace. These guidelines seek to achieve a balance between employees’ wishes for privacy and the need for employers to run their businesses efficiently. The code does not prevent monitoring, but is based on the concept of proportionality. Proportionality means that any adverse impacts from monitoring must be justified by the benefits to the employer and others. This addresses an apparent anomaly in that data protection law refers to individual consent for processing of personal data being ‘freely given’ and it is not normal for employees to give this consent. The code makes it clear that individual consent is not required provided that an organization has undertaken an ‘impact assessment’ of monitoring activities.
According to the code, an impact assessment involves:
- identifying clearly the purpose(s) behind the monitoring arrangement and the benefits it is likely to deliver
- identifying any likely adverse impact of the monitoring arrangement
- considering alternatives to monitoring or different ways in which it might be carried out
- taking into account the obligations that arise from monitoring
- judging whether monitoring is justified.
The code does not make specific recommendations about monitoring of e-mails or web traffic, but it does refer to them as typical monitoring activities which it suggests may be acceptable if staff are informed of them and an impact assessment has been conducted. The code does ask employers to consider whether alternatives may be better than systematic monitoring. Alternatives may include training or clear communication from managers and analysis of stored e-mails where it is thought an infringement has taken place rather than continuous monitoring. For example, automated monitoring is preferred to IT staff viewing personal e-mails of staff. The code also makes clear that the company should not undertake any covert monitoring; so it should be open about all the types of monitoring that occur. In universities, as mentioned above, at log-in, or in computer labs and libraries there is often a notice about ‘acceptable-use policy’. This will describe the types of material it is not acceptable to access and is also a means of explaining monitoring procedures. It does appear, that if an employee was disciplined or dismissed for sending too many personal e-mails for instance, they would have legitimate grounds to appeal if they had not been informed that monitoring was occurring and their managers had not made it clear that this was acceptable practice.
Other European countries have different laws on monitoring. Some such as Germany are much more restrictive than the UK in terms of the level of monitoring that organizations are able to perform. Organizations opening offices abroad clearly need to be aware of local variations in legal constraints on employee monitoring and data protection.
4. E-mail management
E-mail is now an essential business communication tool and is also widely used for personal use. The popularity of e-mail as a communication tool has resulted in billions of messages being sent each day. For the individual, managing these communications in their e-mail inbox is rapidly becoming impossible! For the information services manager and indeed any business manager, there are three main controls that need to be considered to reduce the amount of time effectively wasted by staff reading e-mail. Controls can be introduced as part of an e-mail management policy to minimize the volume of:
- Spam (unsolicited e-mail).
- Internal business e-mail.
- External business e-mail.
- Personal e-mail (friends and family).
Despite the potential time loss through e-mail misuse an AMA (2003) survey suggested that only 34% of employers had a written e-mail retention and deletion policy in place. Furthermore, there are issues of legal liability about what employees say in their e-mail which also need to be considered. We will look at the risk and controls of each e-mail risk in turn.
4.1. Minimizing spam (unsolicited e-mail)
Spam is now a potential problem for every company and individual using the Internet. At the time of writing over 75% of e-mails were spam or virus-related in some countries and individuals whose inboxes are unprotected can receive hundreds of spam e-mails each day. The spammers rely on sending out millions of e-mails often from botnets of infected PCs in the hope that even if there is only a 0.01% response they may make some money, if not necessarily get rich.
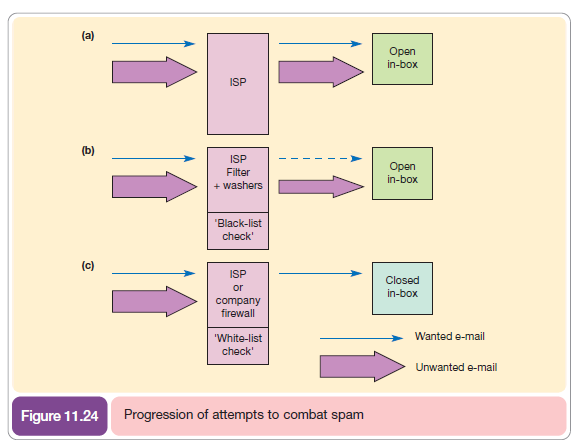
Legal measures to combat spam have had limited success. So, many information services managers are now using a range of methods to control spam. Figure 11.24 summarizes alternative techniques to combat spam. Figure 11.24(a) is the original situation where all mail is allowed into an inbox. Figure 11.23(b) uses different techniques to reduce the volume of e-mail through identification and blocking of spam. Figure 11.24(c) is a closed inbox where only known, trusted e-mails are allowed into an organization.
The full range of techniques that can be used in combination to combat spam include:
- Avoid harvesting of addresses. Spammers harvest e-mails from e-mail addresses published on web pages and even the program code used to convert online form content to an e-mail to a company. By reducing the number of e-mail addresses published, or changing their format, the number of e-mail addresses can be reduced.
- Educate staff not to reply to spam. The worst thing an individual can do on receiving spam is to reply to it to complain or to attempt to unsubscribe. This merely confirms to the spammer that the address is valid and they are likely to send more junk e-mail and sell your address on to other spammers. In Microsoft Outlook images are not enabled since downloading images in an HTML e-mail is a sign to spammers that yours is a valid address.

- Use filters. Filtering software can identify spam from key words and phrases such as ‘For Free’, ‘Sex’ or ‘Viagra’ contained in the subject line, from address and body copy of the e-mail. E-mail filters are provided for users of web-based e-mail such as Hotmail and Yahoo! Mail with e-mails placed in a junk mail folder. Microsoft Outlook Express has its own filter. Filtering software such as Mailwasher (mailwasher.net), Mcaffee Spamkiller (www.mcaffee.com) can also be installed. Unfortunately, many spammers know how to avoid the keywords in the filters. The problem with filters and other services is that there can be ‘false positives’ or valid e-mails that are classified as junk. Additionally, spammers find ways to work around filters by putting ‘gobbeldy gook’ in the footer of their messages that is not recognized by the filters or using variants of words such as Viagra, or Via-gra. Review of these may still be necessary. This technique is represented by Figure 11.24(b).
- Use ‘peer-to-peer’ blocking services. These take advantage of humans being good at identifying spam and then notifying a central server which keeps an index of all spam. CloudMark (cloudmark.com), a peer-to-peer solution, requires users to identify spam by pressing a ‘Block’ button in Outlook Express which then updates a central server, so when others download the same message at a later time, it is automatically identified as spam. This technique is represented by Figure 11.24(b).
- Use blacklist services. Blacklists are lists of known spammers such as those reported to Spamhaus Project (spamhaus.com) or SpamCop (www.spamcop.net). They are often used in conjunction with filters to block e-mails. One of the most widely used systems developed by Brightmail (www.brightmail.com) uses a global network of e-mail addresses set up to trap and identify spam. Brightmail is increasingly used by ISPs such as BT OpenWorld to block spam, but it is not a cheap service, costing $5 to $15 per year. This price could easily be justified by the time staff save over the year. This technique is also represented by Figure 11.24(b).
- Use whitelist services. The whitelist approach has not been adopted widely since it is difficult to set up, but it probably offers the best opportunity for the future. An increasing problem for companies using e-mail for marketing is ‘false positives’ – where filters identify their legitimate e-mail as spam. Whitelist services are one solution to this. A whitelist
gives a list of bona fide e-mail addresses that are likely to want to contact people within an organization. It will include all employees, partners, customers and suppliers who have obtained opt-in from employees to receive e-mail. E-mail from anyone not on the list will be blocked. However, maintaining such as list will require new software and new procedures for keeping it up-to-date. One approach that has been developed in the US is the concept of a ‘bonded sender’ developed by Ironport (bondedsender.com). Senders of opt-in e-mail post a financial bond to prove they are a reputable company. Another service rapidly gaining acceptance is Habeas (www.habeas.com) where special text (a ‘warrant mark’) is sent in outbound mail, which allows filtering systems to identify the e-mail as ‘not spam’. This technique is represented by Figure 11.24(c).
Providers such as Sendmail (www.sendmail.com), GoodMail (www.goodmail.com) and the Yahoo!-sponsored DomainKeys and Microsoft-sponsored Sender Policy Framework have developed ‘sender authentication technology’ which allows organizations to verify the source of a message before accepting it by automatically checking if it came from where it claims it did.
A further approach is challenge/respond. Here, if a message is received from a person who is not on the whitelist, a message is sent to that person requesting that they click on a link to verify that they are a genuine person and not a spammer (spammers would not have time to verify all addresses since it cannot be done automatically). Of course, this presents a problem for legitimate commercial e-mail marketers.
- Ensure anti-virus software and blocking is effective. E-mail viruses are increasingly perpetrated by spammers since they are a method of harvesting e-mail addresses. Virus protection needs to be updated daily with new signatures if addresses are not to be captured through viruses.
4.2. Minimizing internal business e-mail
The ease and low cost of sending e-mails to a distribution list or copying people in on a message can lead to each person in an organization receiving many messages each day from colleagues within the organization. This problem tends to be worse in large organizations, simply because each individual has a larger address book of colleagues.
A press release from the British Computer Society summarizing research conducted by the Henley Management College released on 20 December 2002 suggested that a lot of time is wasted by managers when processing irrelevant e-mails. It suggested that ‘UK management is now suffering acute stress from “Information Overload”’ with executives, ‘complaining of being deluged by e-mail that demands a daily average of two hours of executive time’; particularly frustrating is that nearly a third of e-mail received is deemed to be irrelevant and much is rated of poor quality. Further findings included:
- Of seven common management tasks, meetings took up 2.8 hours on average, dealing with e-mail came second with an average of 1.7 hours and accessing information from the Internet accounted for a further 0.75 hour.
- Respondents reported receiving on average 52 e-mails per day while 7 per cent received 100 e-mails per day or more.
- Managers reported that less than half of e-mails (42 per cent) warranted a response, 35 per cent were read for information only and nearly a quarter were deleted immediately. On average only 30 per cent of e-mails were classified as essential, 37 per cent as important and 33 per cent as irrelevant or unnecessary.
- Despite the reservations about the quality and volume of e-mails received the majority of respondents (81 per cent) regarded e-mail as the communications technology which has had the most positive impact on the way they carried out their job, alongside the Internet and the mobile phone.
To overcome this type of business e-mail overuse, companies are starting to develop e-mail policies which explain best practice. For example, considering the way that the authors of Chaffey and Wood (2005) use their e-mail, we quickly devised these guidelines:
- Only send the e-mail to employees for which it is essential to inform or act upon;
- Banning certain types of e-mails, such as the classic ‘e-mail to the person who sits next to you’ or individuals in the same office (although there are strong arguments for this since e-mail is an asynchronous medium and colleagues are not always available or don’t wish to be disturbed);
- Avoid ‘flaming’ – these are aggressive e-mails which often put voice to feelings that wouldn’t be said face-to-face. If you receive an annoying e-mail it is best to wait 10 minutes to cool down rather than ‘flaming’ the sender;
- Avoid ‘trolls’ – these are a species of e-mail closely related to flame-mails. They are postings to a newsgroup deliberately posted to ‘wind up’ the recipient. They are best ignored;
- Combine items from separate e-mails during the day or week into a single e-mail for the day/week;
- Write clear subject lines;
- Structure e-mails so that they can be scanned quickly using sub-heads and numbered and bulleted lists;
- Make follow-up actions clear;
- When reading e-mail, use folders to categorize e-mails according to content and priority;
- Perform e-mail reading and checking in batches, e.g. once per morning or afternoon rather than being alerted to and opening every e-mail that arrives;
- Delete e-mails which are not required for future reference (large volumes are taken up on servers through staff not deleting e-mails and their attachments);
- And so on – all common-sense guidelines, but often common sense isn’t common!
4.3. Minimizing external business e-mail
As well as spam which is unsolicited and usually untargeted, people within an organization can also receive many e-mails from legitimate suppliers. For example, an IT manager might receive e-mails from hardware and software manufacturers, service providers, event or conference organizers and e-newsletters from magazines. These sources of e-mail are not usually controlled through company e-mail policies; it is usually left to the judgement of the individual employee to select appropriate e-newsletters. The technologies to block e-mails, such as spam filters, will not usually block such messages, but primitive filters may, if they block words such as ‘Offer’ or ‘Free’ which also appear in legitimate business e-mails. The chal- lenge/respond system will still enable such e-mails to be received. Additionally, technology described in Chapter 12 is available to block access to certain web sites such as news or entertainment sites, and this software renders e-newsletters less effective since images are not downloaded from blocked sites. An approach used by many individuals to help control information from these sources is to use a separate e-mail address from the main inbox when opting in. This could be a Hotmail or Yahoo! Mail address and this form of e-newsletter can be read at the office or at home and is also available when the individual changes jobs.
4.4. Minimizing personal e-mail (friends and family)
Although there are many surveys about the volume of spam and amount of time spent processing e-mail at work, there is relatively little data published on the amount of time spent writing personal e-mails. Most of it is not independent; it is commissioned by vendors of software for monitoring e-mail use. However, using e-mail for personal use is going to occur if there are no measures to stop it.
To minimize this problem and some of the problems of over-using e-mail for business use, the following steps can be taken:
- Create written guidelines defining the policy on acceptable e-mail use and disciplinary procedures for when guidelines are breached;
- Use increasing levels of control or sanctions for breaches including performance reviews, verbal warnings, removal of e-mail privileges, termination and legal action;
- Providing training for staff on acceptable and efficient e-mail use;
- Monitor e-mails for signatures of personal use and any breaches of the policy, e.g. swearing, and take action accordingly.
5. Hacking
‘Hacking’ refers to the process of gaining unauthorized access to computer systems, typically across a network. Hacking can take different forms. Hacking for monetary gain is usually aimed at identity theft where personal details and credit card details are accessed for the purpose of fraud. Hacking could also occur with malicious intent. For example, a former employee might gain access to a network with a view to deleting files or passing information on to a competitor. Some of the notorious hackers who have been prosecuted, but often seem to have ultimately gained from their misdemeanours, are:
- Robert Morris – The son of the chief scientist at the US National Computer Security Center, this graduate student created a destructive Internet worm in 1988 which took advantage of a security flaw in the Unix operating system. When unleashed it caused thousands of computers to crash. The disruption was partly accidental and he released instructions to system administrators on how to resolve the problem. He was sentenced to three years of probation, 400 hours of community service and a fine of $10,050. He is now an assistant professor at MIT, where he originally released his worm to disguise its creation at Cornell University.
- Kevin Poulsen – In 1990 Poulsen took over all telephone lines into the Los Angeles radio station KIIS-FM, assuring that he would be the 102nd caller. Poulsen won a Porsche 944 S2. This was one of many hacks conducted while he worked for hi-tech company SRI International by day and hacked at night. He was eventually traced and, in June 1994, he pleaded guilty to seven counts of mail, wire and computer fraud, money laundering and obstruction of justice, and was sentenced to 51 months in prison and ordered to pay $56,000 in restitution. It was the longest sentence ever given for hacking. He is now a computer security journalist.
- Kevin Mitnick – The first hacker to be featured on an FBI ‘Most wanted’ poster, Mitnick was arrested in 1995. He later pleaded guilty to four counts of wire fraud, two counts of computer fraud and one count of illegally intercepting a wire communication. He admitted that he broke into computer systems and stole proprietary software belonging to Motorola, Novell, Fujitsu, Sun Microsystems and other companies. He was sentenced to 46 months. Following his sentence he became a security consultant and is now a leading commentator on security and has made many TV appearances and written books and articles.
- Vladimir Levin – A graduate mathematician who was part of a Russian gang that reputedly masterminded a $10 million fraud of Citibank. Arrested by Interpol at London’s Heathrow Airport in 1995.
- Alexey Ivanov – A June 2001 indictment against Ivanov alleged that he gained unauthorized access into CTS Network Services, a San Diego-based Internet service provider. Ivanov allegedly used a stolen credit card number to open an account with CTS, and once inside the company’s computers hacked the systems to gain control of the computers. He then used CTS computers to launch a series of computer attacks against e-commerce companies, including two credit card processors – Sterling Microsystems of Anaheim and Transmark of Rancho Cucamonga – and NaraBank of Los Angeles. Ivanov allegedly stole customer financial information, such as credit card and bank account numbers, leading to fraud of $25 million. A prison sentence of three years was given.
Hacking may not be directly related to theft or damage, but gaining access to a system may be perceived by the hacker as a technical challenge. The term ‘hacking’ traditionally refers to the process of creating program code, another form of technical challenge. This can almost be considered as a pastime, albeit an unethical one. While not as popular as watching sports,
hacking appears to be more than one or two people in each country. BBC (2003) reports that TruSecure, a US hacking monitoring organization, currently tracks more than 11,000 individuals in about 900 different hacking groups and gangs.
Three main forms of gaining unauthorized access to computer systems can be identified. First, the normal entry points to systems through usernames and passwords can be used. For example, many system log-ins have a username of ‘administrator’ by default. Sometimes the password will be the same. Other common passwords are days of the week or children’s names. Tools are available to try different alternative log-ins, although most modern systems will refuse access after several attempts. Hacking can be combined with identity theft to gain an idea of the passwords used.
The second form of hacking exploits known vulnerabilities in systems. Although these vulnerabilities in operating systems such as Windows or Linux or web browsers such as Internet Explorer are publicly known and will be posted on the vendor’s web site and specialist security web sites, there will be many system administrators who have not updated their systems with the latest security update or ‘patch’. This is partly because there are so many security vulnerabilities, with new ones being announced every week.
Thirdly, Kevin Mitnick refers to ‘social engineering’ which typically involves impersonating employees of an organization to access security details. One example of this, given in Mitnick and Simon (2002), is when the attacker contacts a new employee and advises them of the need to comply with security policies. The attacker then asks the user for their password to check it is in line with the policy of choosing a difficult-to-guess password. Once the user reveals their password, the caller makes recommendations to construct future passwords in such a way that the attacker will be able to guess them.
Protecting computer systems against hackers
Protecting computer systems against hackers involves creating counter-measures to the three main types of hacking outlined above. For gaining access to systems via passwords, policies can be developed to reduce the risk of access. One simple approach is to mandate that new passwords are required every month and that they contain at least one number and a mix of upper and lower case. This prevents users using simple passwords which are easily guessed. Education is required to reduce the risk of passwords falsely obtained through ‘social engineering’, but this will never completely remove the threat.
Computer systems can also be protected by limiting access at the point the external network enters the company. Firewalls are essential to prevent outside access to confidential company information, particularly where an extranet has been set up. Firewalls are usually created as software mounted on a separate server at the point where the company is connected to the Internet. Firewall software can then be configured to only accept links from trusted domains representing other offices in the company.
Measures must also be put in place to stop access to systems through published security vulnerabilities. BBC (2003) reported that in 2003 there were 5,500 security vulnerabilities that could be used. A policy on updating operating systems and other software with the latest versions is also required. It is not practical to make all updates, but new vulnerabilities must be monitored and patches applied to the highest-risk categories. This is a specialist task and is often outsourced. TruSecure (www.trusecure.com) is an example of a specialist company that monitors security vulnerabilities and advises organizations on prevention. TruSecure estimates that only 80 or 90 per cent of vulnerabilities are being used regularly, so patches should prioritize on these. TruSecure provides a service for hundreds of organizations to see whether they possess these vulnerabilities. They also employ a team of people who attempt to infiltrate hacker groups to determine the latest techniques. TruSecure gave the FBI over 200 documents about the ‘Melissa’ virus author. Although they did not know his real name, they knew his three aliases and had built a detailed profile of him.
A further approach organizations use to check their defences against hacking is to employ ‘ethical hackers’. These are former hackers who now apply their skills to test the vulnerabilities of existing systems.
Although all of the examples of hacking above involve computer network, sometimes ‘low-tech’ techniques can be used too. Guardian (2003) reported cases where criminals had impersonated call-centre staff in order to gain access to customer accounts!
6. Secure e-commerce transactions
For e-businesses offering online sales there are also additional security risks from the customer or merchant perspective:
- Transaction or credit card details stolen in transit.
- Customer’s credit card details stolen from merchant’s server.
- Merchant or customer is not who they claim to be.
In this section we assess the measures that can be taken to reduce the risk of these breaches of e-commerce security. We start by reviewing some of the theory of online security and then review the techniques used.
Principles of secure systems
Before we look at the principle of secure systems, it is worth reviewing the standard terminology for the different parties involved in the transaction:
- These are the consumers buying the goods.
- These are the retailers.
- Certification authority (CA). This is a body that issues digital certificates that confirm the identity of purchasers and merchants.
- These are traditional banks.
- Electronic token issuer. A virtual bank that issues digital currency.
The basic requirements for security systems from these different parties to the transaction are as follows:
- Authentication – are parties to the transaction who they claim to be (risk (c) above)?
- Privacy and confidentiality – are transaction data protected? The consumer may want to make an anonymous purchase. Are all non-essential traces of a transaction removed from the public network and all intermediary records eliminated (risks (b) and (c) above)?
- Integrity – checks that the message sent is complete, i.e. that it is not corrupted.
- Non-repudiability – ensures sender cannot deny sending message.
- Availability – how can threats to the continuity and performance of the system be eliminated? Kesh (2002) explore the security requirements for e-commerce in more detail.
7. Approaches to developing secure systems
7.1. Digital certificates
There are two main methods of encryption using digital certificates.
- Secret-key (symmetric) encryption
Symmetric encryption involves both parties having an identical (shared) key that is known only to them. Only this key can be used to encrypt and decrypt messages. The secret key has to be passed from one party to the other before use in much the same way as a copy of a secure attache case key would have to be sent to a receiver of information. This approach has traditionally been used to achieve security between two separate parties, such as major companies conducting EDI. Here the private key is sent out electronically or by courier to ensure it is not copied.
This method is not practical for general e-commerce, as it would not be safe for a purchaser to give a secret key to a merchant since control of it would be lost and it could not then be used for other purposes. A merchant would also have to manage many customer keys.
- Public-key (asymmetric) encryption
Asymmetric encryption is so called since the keys used by the sender and receiver of information are different. The two keys are related by a numerical code, so only the pair of keys can be used in combination to encrypt and decrypt information. Figure 11.25 shows how public-key encryption works in an e-commerce context. A customer can place an order with a merchant by automatically looking up the public key of the merchant and then using this key to encrypt the message containing their order. The scrambled message is then sent across the Internet and on receipt by the merchant is read using the merchant’s private key. In this way only the merchant who has the only copy of the private key can read the order. In the reverse case the merchant could confirm the customer’s identity by reading identity information such as a digital signature encrypted with the private key of the customer using their public key.
Pretty Good Privacy (PGP) is a public-key encryption system used to encrypt e-mail messages.
7.2. Digital signatures
Digital signatures can be used to create commercial systems by using public key encryption to achieve authentication: the merchant and purchaser can prove they are genuine. The purchaser’s digital signature is encrypted before sending a message using their private key and, on receipt, the public key of the purchaser is used to decrypt the digital signature. This proves the customer is genuine. Digital signatures are not widely used currently due to the difficulty of setting up transactions, but they will become more widespread as the public-key infrastructure (PKI) stabilizes and use of certificate authorities increases.
7.3. The public-key infrastructure (PKI) and certificate authorities (CAs)
In order for digital signatures and public-key encryption to be effective it is necessary to be sure that the public key intended for decryption of a document actually belongs to the person you believe is sending you the document. The developing solution to this problem is the issuance by a trusted third party (TTP) of a message containing owner identification information and a copy of the public key of that person. The TTPs are usually referred to as ‘certificate authorities’ (CAs), and various bodies such as banks and the Post Office are likely to fulfil this role. That message is called a ‘certificate’. In reality, as asymmetric encryption is rather slow, it is often only a sample of the message that is encrypted and used as the representative digital signature.

Example certificate information could include:
- user identification data;
- issuing authority identification and digital signature;
- user’s public key;
- expiry date of this certificate;
- class of certificate;
- digital identification code of this certificate.
It is proposed that different classes of certificates would exist according to the type of information contained. For example:
- name, e-mail address
- driver’s licence, national insurance number, date of birth
- credit check
- organization-specific security clearance data.
7.4. Virtual private networks
A virtual private network (VPN) is a private wide-area network that runs over the public network, rather than a more expensive private network. The technique by which VPN operates is sometimes referred to as ‘tunnelling’, and involves encrypting both packet headers and content using a secure form of the Internet Protocol known as IPSec. As explained in Chapter 3, VPNs enable the global organization to conduct its business securely, but using the public Internet rather than more expensive proprietary systems.
8. Current approaches to e-commerce security
In this section we review the approaches used by e-commerce sites to achieve security using the techniques described above.
8.1. Secure Sockets Layer Protocol (SSL)
SSL is a security protocol, originally developed by Netscape, but now supported by all browsers such as Microsoft Internet Explorer. SSL is used in the majority of B2C e-commerce transactions since it is easy for the customer to use without the need to download additional software or a certificate.
When a customer enters a secure checkout area of an e-commerce site SSL is used and the customer is prompted that ‘you are about to view information over a secure connection’ and a key symbol is used to denote this security. When encryption is occurring they will see that the web address prefix in the browser changes from ‘http://’ to ‘https://’ and a padlock appears at the bottom of the browser window.
How does SSL relate to the different security concepts described above? The main facilities it provides are security and confidentiality. SSL enables a private link to be set up between customer and merchant. Encryption is used to scramble the details of an e-commerce transaction as it is passed between sender and receiver and also when the details are held on the computers at each end. It would require a determined attempt to intercept such a message and decrypt it. SSL is more widely used than the rival S-HTTP method.
The detailed stages of SSL are as follows:
- Client browser sends request for a secure connection.
- Server responds with a digital certificate which is sent for authentication.
- Client and server negotiate session keys, which are symmetrical keys used only for the duration of the transaction.
Since, with enough computing power, time and motivation, it is possible to decrypt messages encrypted using SSL, much effort is being put into finding more secure methods of encryption such as SET. From a merchant’s point of view there is also the problem that authentication of the customer is not possible without resorting to other methods such as credit checks.
8.2. Certificate authorities (CAs)
For secure e-commerce, there is a requirement for the management of the vast number of public keys. This management involves procedures and protocols necesssary throughout the lifetime of a key – generation, dissemination, revocation and change – together with the administrative functions of time/date stamping and archiving. The successful establishment of a CA is an immense challenge of trust building and complex management. There are two opposing views on how that challenge should be met:
- Decentralized: market-driven, creating brand-name-based ‘islands of trust’ such as the Consumers Association. There is a practical need for a local physical office to present certificates of attestable value, e.g. passports, drivers’ licences. Banks and the Post Office have a huge advantage.
- Centralized: in the UK, the Department of Trade and Industry (DTI) has proposed a hierarchical tree leading ultimately to the government.
The best-known commercial CA is Verisign (www.verisign.com) and this is commonly used for merchant verification. For example, the Avon site uses Verisign to prove to its customers that it is the genuine site. Post Offices and telecommunications suppliers are also acting as CAs. Examples in the UK include BT (Trust Wise) and the Post Office (ViaCode).
9. Reassuring the customer
Once the security measures are in place, content on the merchant’s site can be used to reassure the customer, for example Amazon (www.amazon.com) takes customer fears about security seriously, judging by the prominence and amount of content it devotes to this issue. Some of the approaches used indicate good practice in allaying customers’ fears. These include:
- use of customer guarantee to safeguard purchase;
- clear explanation of SSL security measures used;
- highlighting the rarity of fraud (‘ten million customers have shopped safely without credit card fraud’);
- the use of alternative ordering mechanisms such as phone or fax;
- the prominence of information to allay fears – the guarantee is one of the main menu options.
Companies can also use independent third parties that set guidelines for online privacy and security. The best-known international bodies are TRUSTe (www.truste.org) and Verisign for payment authentication (www.verisign.com). Within particular countries there may be other bodies such as, in the UK, ISIS or Internet Shopping is Safe scheme (http://isis.imrg.org)
Source: Dave Chaffey (2010), E-Business and E-Commerce Management: Strategy, Implementation and Practice, Prentice Hall (4th Edition).

I was suggested this web site by my cousin. I am not sure whether this post is written by him as nobody else know such detailed about my difficulty. You are wonderful! Thanks!